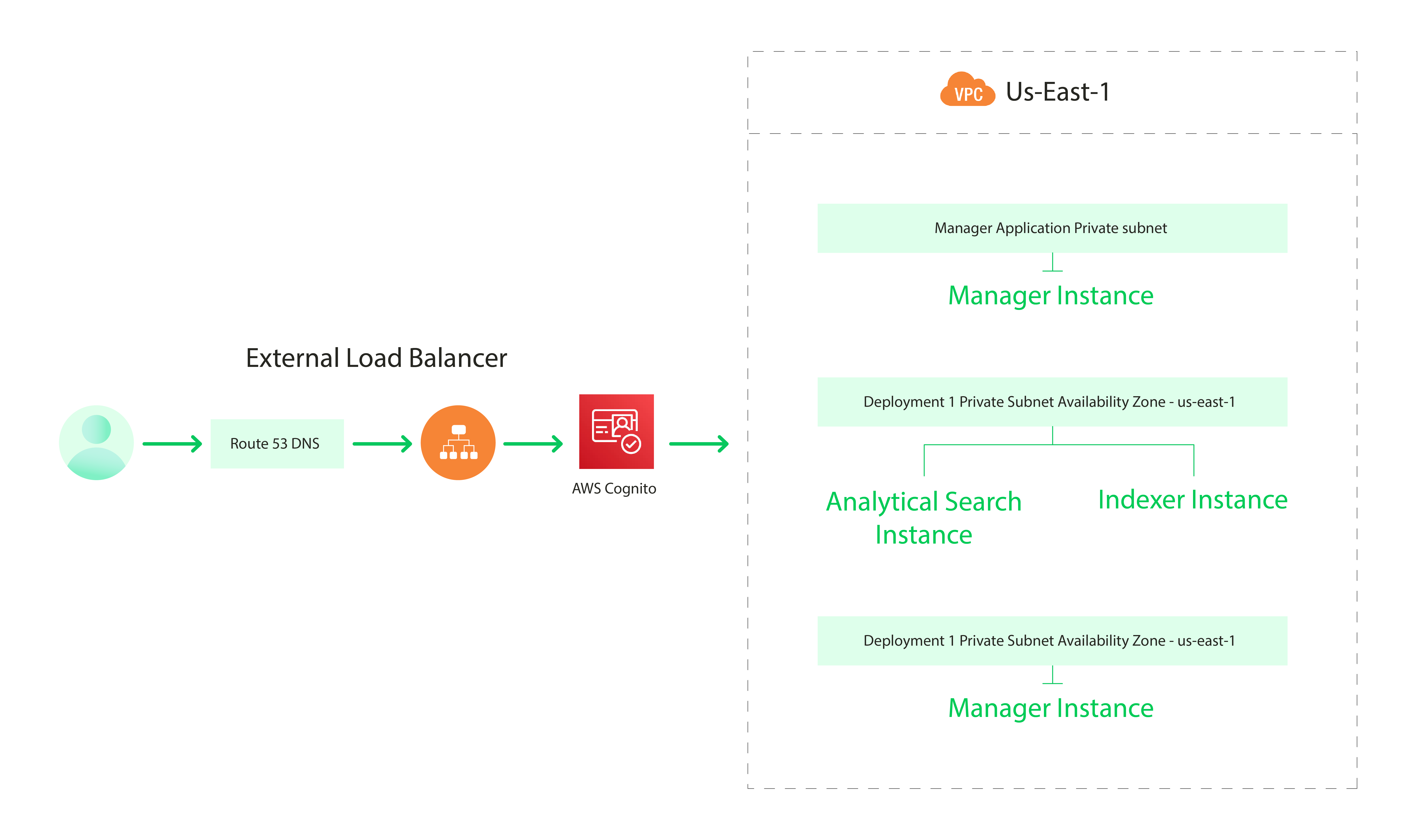
There are 3 types of requests directed towards your Q-Sensei Logs SaaS application:
- Upload API requests to upload events: We use an Upload API Gateway to securely send events to your deployment. Please refer the section on Single Deployments Architecture.
- UI Access to access the Manager UI and Analytical UI.
- API requests generated from the Manager UI and Analytical UI.
For the last 2 request types, let us zoom out and see a typical request flow.
- A user accesses the application hosted at https://example.logs.qsensei.cloud.
- The request goes to a AWS Route53 Domain Name Service where the domain name is resolved and the request is forwarded to an Internet facing Application Load balancer.
- All requests which are forwarded to the Application Load balancer are first authenticated and authorized using AWS Cognito.
- If it is a valid request, the user request is either forwarded to the backend Manager UI or the Analytics UI depending on the user role.
AWS Virtual Private Cloud (VPC) and Private Subnet
A Q-Sensei Logs SaaS deployment is created in an AWS Virtual Private Cloud (VPC). Each deployment is created in a logically isolated virtual network. Having a VPC allows us to use multiple layers of security:
- Each EC2 instance is part of a private subnet with no internet access.
- Each EC2 instance is part of a security group that acts as a virtual firewall to control incoming and outgoing traffic.
- The private subnet has an associated network access control list (ACL), an additional layer of security that acts as a firewall for the private subnet in which the deployment is created.
- The only way to forward requests to the backend instances is via the Application Load Balancer which authenticates each and every incoming request using AWS Cognito.
AWS Cognito
Amazon Cognito helps you meet multiple security and compliance requirements, including those for highly regulated organizations such as healthcare companies and merchants. Amazon Cognito is HIPAA eligible and PCI DSS, SOC, and ISO/IEC 27001, ISO/IEC 27017, ISO/IEC 27018, and ISO 9001.
Encryption
All data in transit as well as at rest is encrypted.